
ArkStream Capital: Details on zk's investment opportunities in the Expansion and privacy circuit (I)
ArkStream Capital: An Overview of zk's Investment Opportunities in the Expansion and Privacy Circuit (Part I)
Original article by Ray
ArkStream Capital public account
preamble
In the current Bitcoin network or Ethereum network, there are a lot of transactions waiting for blocks to be packaged. This mechanism of waiting for confirmation of transactions has greatly dampened the user experience, and transaction congestion is now an urgent problem for the entire industry to solve. In addition, due to the transparency of blockchain itself, once the address is marked, all of our transactions have no privacy at all. As DeFi grows, the need for privacy in this dark forest of cryptocurrencies has never been more urgent. In the DeFi building blocks on the verge of collapse, the chain clearly visible clearing line and fixed point burst warehouse has become an important driving force for the price to stop falling.
The conundrum of concurrency and privacy has been explored for years by geeks and developers alike. Zero-knowledge proof technology, by its own unique nature, is as important to blockchain technology as transparency, decentralization, and imtamperability, bringing solutions to scalability and privacy issues in its own right. This paper will start from the definition and implementation of zero-knowledge proof, take many popular projects in the market as examples, explore its exploration in the two fields of expansion and privacy protection, and think about the investment opportunities from the perspective of investment institutions.
Definition of zero-knowledge proof
People tend to believe what they see and hear in the course of life. However, when it comes to valuable information, or knowledge, the owner wants to convince others that he or she has ownership of the knowledge without disclosing the core secrets. To solve this need, zero-knowledge proof comes into being. To use a more academic expression, zero-knowledge proof is the proof and verification of "knowledge is true" by two approaches, in which the owner of knowledge is the proof party, and the other party is the verification party.
We use a sketch to visually explain what zero-knowledge proofs can achieve.
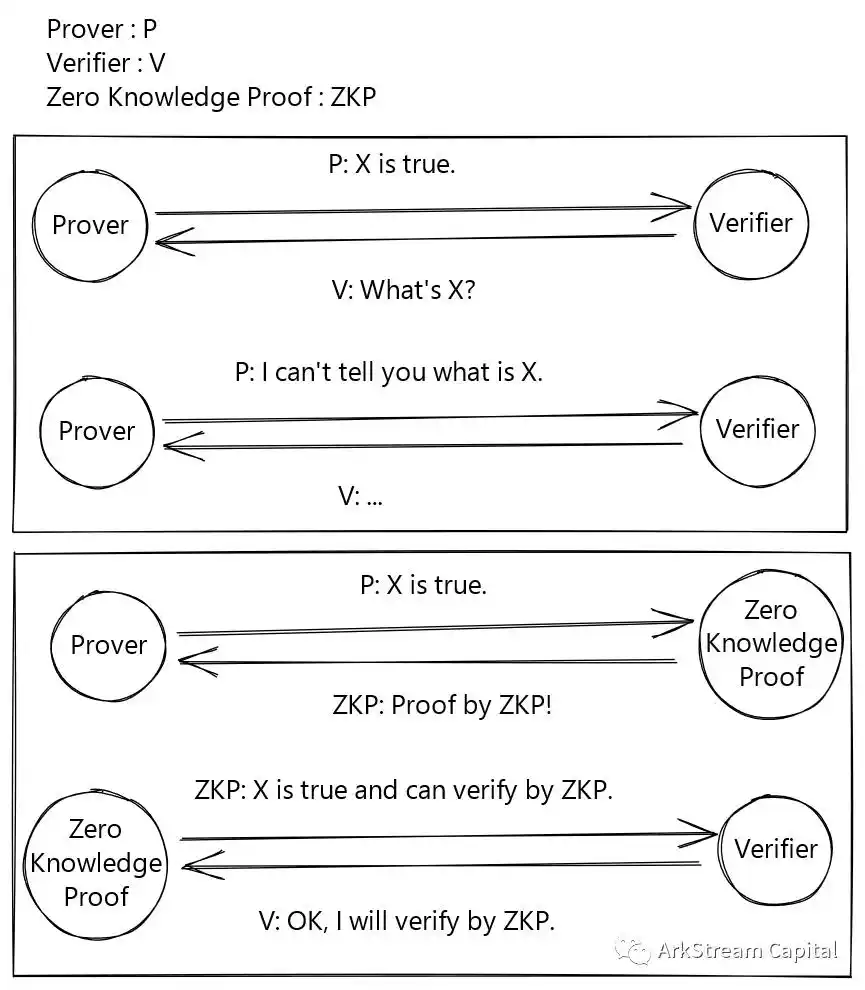
Figure 1: Proof without ZKP and with ZKP
From this graph, we can extract three properties of zero-knowledge proof:
Complete:诚实的证明方,对「知识为真 」这一论断进行证明,肯定可以让验证方信服。
(Sound):证明方无法将「 知识为假 」证明成「知识为真」。
Zero Knowledge:整个证明,验证方除了「 知识为真」这一论断,不会获得其他与知识相关的机密。
These three properties in plain English, that is: true can not be false; False is not true; The unknown is real, the unknown is still unknown. Third sex in a more general way, I said "what's true," you proved "what's true," but you don't know what's what.
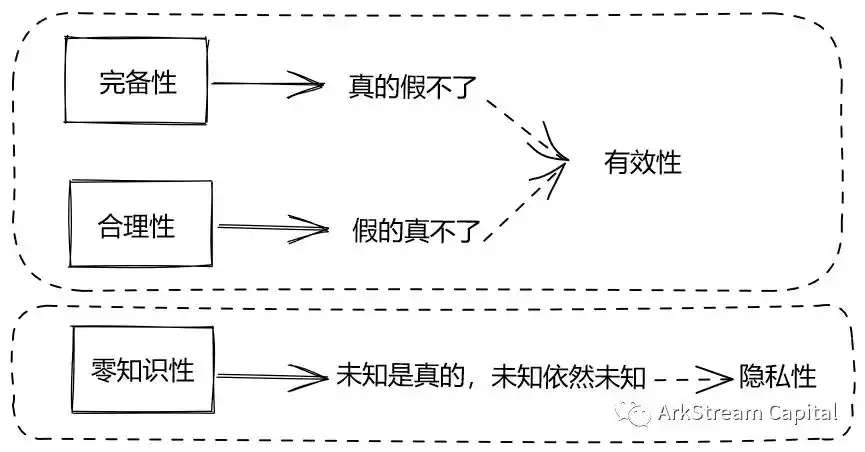
Figure 2: Zero knowledge proves three properties and two properties
The first two properties are easier to understand and notice than the third, which is easily confused and ignored.
When both sides of proof and verification know the content of knowledge, it is easy to verify that "knowledge is true", but it can no longer satisfy the requirement of proof of zero knowledge. On the contrary, if zero knowledge is satisfied, it is difficult for us to verify. Think about it, how do we know that nothing is being revealed in the process of proof and verification? Does the verifier believe the knowledge is true if it is not disclosed? After all, he does not even know what knowledge is, or even, perhaps, whether it exists at all! But the fact is, knowledge must exist, on the contrary, the proof of "knowledge is true" is not initiated at all!
We use more specific examples to talk about, for example, we all believe that Satoshi Nakamoto must exist in the world, otherwise, bitcoin would not appear, but after so many years, we do not know whether Satoshi Nakamoto alive in the world. If Satoshi Nakamoto is still alive, and he wants to tell the world that he is still alive. So, Satoshi Nakamoto can use zero knowledge proof to pass to the world "I am still alive", at this time the world in accordance with zero knowledge proof that this information, but will not know whether Satoshi Nakamoto has used the private key, whether to land the BitcoinTalk account self-certification. Another scenario is that Nakamoto Satoshi in the invention of bitcoin, the creation address is to have the first bitcoin, when the address uses the corresponding private key for activities, the same can pass Nakamoto Satoshi is still alive information, but this no longer meets the zero knowledge, because, the world knows that Nakamoto Satoshi is still alive, because his private key activities.
To put it simply,Zero-knowledge proof can not only guarantee the privacy of knowledge, but also guarantee the validity of knowledge. These two points directly determine the two types of application scenarios of zero-knowledge proof in the crypto world: privacy and enlargement.Of course, there will be more subdivided applications in the privacy scenario, such as privacy payment, anonymous voting and even privacy public chain, which can also be generally understood as asset payment privacy and logic universal privacy. As for the expansion scenario, the completeness and rationality of zero-knowledge proof and other technical means are used to achieve it.
Realization of zero-knowledge proof
Zero-knowledge proof is invented and realized by using a lot of mathematics and cryptography knowledge.In the whole proof realization, according to interaction or not, can be divided into interactive proof and non-interactive proof. Interactive proof is a proof process that requires the prover and verifier to alternate according to some order and rules, and then complete the proof by random probability. Non-interactive proof means that the prover calculates and submits all the proof data in a complete one-time by himself in accordance with the proof rules or proof process, and then the prover can directly verify with these proof data. To put it in an extreme way, a non-interactive proof is to compress multiple steps of an interactive proof into one interaction. In addition, non-interactive proof can be seen as splitting the whole implementation into a proof process and a verification process.
Below, we simulate the difference between interactive and non-interactive proofs using two different scenarios.
Simplified scenario 1, suppose Satoshi Nakamoto's genesis private key reappears in the world, now, to prove that the private key is still active.
The process of interactive proof:
1, the verifier calls the prover of the Genesis private key, and you write a sentence after a certain block height: Hello World.
2. The prover of the creation private key waits for the height of a certain block as required and then sends a message to the whole network: Hello World.
3,验证方在网络里面验证创世私钥是否按照要求在某个区块高度之后留言:Hello World。
4. Repeat steps 1, 2 and 3. When the frequency reaches a certain level, it can be determined from the perspective of probability that the private key is basically active.
Flow of non-interactive proof:
1, some device/emulator/Turing machine generates a shared, random string xyz, then makes this string public, and asks the prover of the Genesis private key to leave a message to the whole network in the form of "xyz, Hello World".
2. Proof of Trands Private key,Follow the rules of the device/simulator/Turing machine", using the string xyz and its own Hello World, leave a message to the whole network: "xyz, Hello World".
3. The verifier takes the string xyz, sees the message for the Genesis private key, and directly determines that the private key is active.
Simplified scenario 2, assuming that Zhang SAN knows Gauss algorithm, Li Si does not.
The process of interactive proof:
1, Li Si talking to Zhang SAN, 1+2+3+ in 30 seconds... +8887+8888.
2. Zhang SAN took the Gauss algorithm, calculated the result in 30 seconds, and told Li Si.
3. Li Si used his simplest addition to test whether the result was correct.
4. Repeat steps 1, 2 and 3. When the frequency reaches a certain level, it can be determined from the perspective of probability.
Flow of non-interactive proof:
1, some device/emulator/Turing machine generates a shared random integer x.
2, Zhang SAN took the Gauss algorithm, directly calculate 1+2+3+... Plus x minus 1 plus x.
3. Li Si uses his simplest addition to check whether the result is correct. If it is correct, Zhang SAN knows the Gaussian algorithm.
From the above example, we can find that non-interactive proof has obvious advantages over interactive proof: 1. It does not depend on a specific interactive prover, and is an excellent solution for one prover to N provers; 2. 2, not limited to the interaction moment, can be carried out at any time. However, we have also noticed the presence of emulators/Turing machines in non-interactive proofs!
Here comes the core concept of zero-knowledge proof: simulator/Turing machine.Simulators/Turing machines can hide knowledge, but still ensure that "knowledge is true" can be proved and verified smoothly.
In order to realize the core functions of non-interactive proof simulator/Turing machine, the current technical solutions are roughly as follows:随机预言(Random Oracle)和公共参考串(Common Reference String、CRS),而其中公共参考串是广泛使用的方案. In our opinion, there is not much essential difference between random prediction and common reference strings. The common reference string CRS must be generated by a trusted third party and then shared with the prover and verifier. Here, the generation of CRS must be guaranteed to be random and reliable, so,The link that generates CRS is also called Trusted Setup, or trusted setup.
We can use God to compare the simulator/Turing machine. God is public, which can not only help the prover hide knowledge and assist the prover to complete the proof, but also identify whether the prover forgery knowledge and assist the prover to successfully verify. God is perfect, but ultimately need to create God, God creation process can be corresponding to: believable Settings. In addition, God is applicable and not necessarily universal, just as Jesus is the Western God and Tathagata is the Eastern God (Applicability of trusted Settings). Further down the line, God can be unreliable. (Security for trusted Settings)
The proof always comes back to the concrete steps. Just as we do with math proof problems, there are steps. For zero-knowledge proof, there's a technical term for this specific step: Circuit.. As for QAP/QSP, Boolean circuits, and arithmetic circuits, we can simply classify them as concrete steps in a non-interactive proof process. There are thousands of mathematical proof problems in the world. When solving the problem, we need to write corresponding steps to solve the problem.Similarly, for zero-knowledge proof under different knowledge, the circuit also needs to be specially written. Of course, there are certain kinds of proof of knowledge that can be simplified by using a common circuit framework.For different mathematical proof problems, we need to write a separate procedure (Special circuit), and for a certain kind of mathematical proof, we can write a general procedure (Universal circuit), or even, for one type of question, we can refer directly to the written procedure/conclusion for another type of question. (Composability/interactivity of circuits).
Follow the previous mathematical proof to the position of the circuit

Figure 3: Analogy of a circuit
As for other concepts or terms, such as first-order constraint systems R1CS, NP Problem, polynomial, knowledge of polynomials, factorization, fuzzy computing, information, knowledge, circuit satisfiability, complete security, Semantic security, indiscriminability, mapping, homomorphism, finite field, cyclic group, Fiat-Shamir transformation, ECDSA signature...... Because it's so conceptual and mathematical,Unless you are an expert in mathematics and cryptography, it is not advisable to expend too much brainpower and energy on this subject. The key information we only need to know is that the different implementation schemes of zero-knowledge proof lie in whether the trusted setting is introduced or not, the applicability of the trusted setting and the difficulty of programming the circuit.
For different zero-knowledge proof implementation schemes, we can use the five dimensions of the time and space cost of the prover and verifier, as well as the security to judge the merits of the implementation schemes.
The time cost of the proof: that is, the calculation time, determines the speed of the proof;
The time cost of the verifier: that is, the verification time;
Space overhead for prover and verifier: existsProof sizeThe concept of ", determines the storage space usage requirements, is also often said the concise reference;
Security: Because some protocols need to introduce trusted Settings, corresponding implementation schemes rely on novelty Settings for security. In addition, there are differences in the applicability of trusted Settings, namely "permanent" and "one-time".
Different implementation schemes eventually divide into two major protocols of zero-knowledge proof: zk-SNARK zero-knowledge concise non-interactive knowledge proof and zk-STARK zero-knowledge extensible transparent knowledge proof.
zk-SNARK: Zero-Knowledge Succint Non-interactive Arguments of Knowledge. Non-interactive proof requires trust setting, and different implementation schemes have different requirements and effects on trust setting. ZCash has been used for many years, and there are many subdivided optimization implementation schemes. Well-known projects include: ZCash, zkSync, Aztec, etc. Due to the long time, a large number of derivative agreements have been born: Schnorr protocol, Pinocchio protocol, Marlin protocol, Sonic protocol, Libra protocol, PLONK protocol, Spartan protocol, BullteProof protocol, etc.
zk-STARK: Zero-Knowledge Scalable Transparent Argument of Knowledge. Non-interactive proof, no need for trusted Settings, anti-quantum computing,Proving size is expensive. The Starkware team has invented and proposed that there are some specialized projects in use, dYdX (recently announced to migrate to Cosmos), Immutable, and Deversifi.
Referring to the saying that blockchain is impossible triangle, the implementation scheme of zero-knowledge proof can be said to be an imperfect triangle. Although all implementation schemes can achieve completeness, rationality and zero-knowledge at the same time, they all have certain trade-offs due to the requirements of application scenarios. Or, more obviously, zero-knowledge implementation can be weakened or even ignored when completeness and rationality are emphasized (expanding Layer2). In addition, zero-knowledge proof itself is not a decentralized property, if this aspect is required, it needs to be combined with decentralized design (even more difficult).
Zero knowledge proof virtual machine
After discussing the different implementation schemes, we will discuss the key to the implementation of the scheme. Applications and products on the Internet today are in high-level programming languages (C++, Java, Rust, Solidity......) The implementation of the program.Virtual machine/interpreterIt's a black box for program execution that converts a program into a language that the machine can recognize and understand, and then runs the program instead of the machine. If there is no virtual machine of zero-knowledge proof, when we use zero-knowledge proof technology to write programs, we need to write the corresponding implementation circuit for the program. Such circuits are difficult and inefficient to write, test, and produce. To do this, zero-knowledge technologies need to be used more widely and efficiently,A zero-knowledge proof version virtual machine (zkVM) that can generate proof submission and verification for programs is a must. Whether the advanced programming languages adopted by zkVM are C++, Java, or specially designed advanced circuit programming languages (Stareware's Cairo, zkSync's Zinc) depends on the design and capabilities of the zkVM. It is important to emphasize that,There is no mandatory blockchain requirement for zkVM.
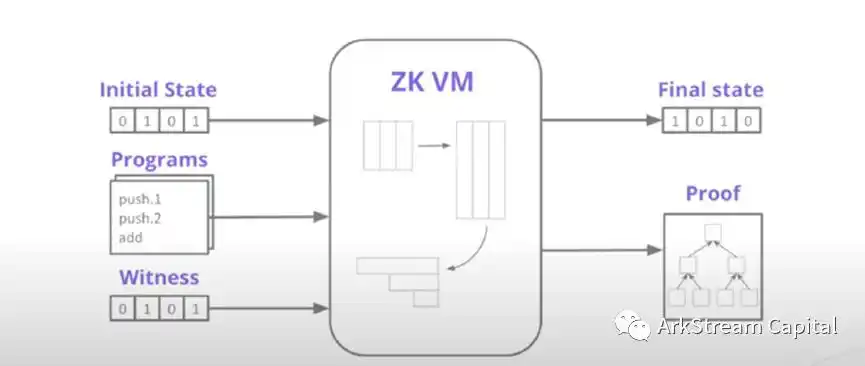
Figure 4:Polygon Miden Deep Dive zkVM
Being able to support programs universally is very important to the zkVM, and the versatility of the zkVM is compromised if only certain kinds of programs can be virtualized. In addition to versatility,Simplicity, recursive usability, composability, and ease of useAre other indicators to consider.
Here are some examples to illustrateRecursive availability:
Problem: Suppose the computer only supports two-digit addition, not multi-digit addition and multiplication, calculate 1+2+3+... Plus 99 plus 100?
Non-recursive version of the solution:
1+2= 3,3 +3= 6,6 +4=10... 4950+100=5050
In total, 99 sums were performed. (The concept of iteration is not introduced here, but interested self-searching learning)
Recursive version solution:
1 + 2 + 3 +... + 99 + 100
Calculate 1 and (2+3+... +99+100), and (2+3+... The calculation of +99+100) can be solved by using this method again, that is, (2+3+... +99+100) is converted to calculate 2 and (3+... +99+100), and so on until the two-digit sum restriction is met, that is, 99+100 = 199, and then 199So let's finish the recursion and figure it out.
Recursive availability allows you to directly reuse the solution to the problem as it is being solved. This can greatly simplify the way to solve practical problems.
We mentioned earlier that there is no hard link between the use of zkVM and blockchain, so next, we will try to explore the combination of zkVM and blockchain. First, let's go back to Ethereum, the world computer that pioneered smart contracts, or more technically, distributed virtual machines. The broad EVM (Ethereum Virtual Machine), which can be equivalent to Ethereum, consists of modules with variable machine state, read-only EVM code, and stored account data. In the narrow sense, EVM can refer to the read-only EVM code and EVM operation code of the Ethereum virtual machine.
For Ethereum, the entire network maintains a consensual state backbone at any given moment, which is determined by the longest block. The transactions in the blocks will drive the state of the Ethereum world. When we complain about the lack of transaction throughput and privacy in the network, the real root cause is the bottlenecks and flaws in the internal components of Ethereum themselves. At this moment, let us have a very beautiful vision, if all modules of the whole ethereum can be zero-knowledge proof, then transaction execution calculation no longer need to be processed by Ethereum, Ethereum simply need to complete the validity of the transaction verification can be, and ethereum internal account data, can be selectively open and transparent according to the need. In this way, the transaction processing power of Ethereum can be greatly freed up, and the privacy of the data on the chain can be guaranteed. With the diversity of current zero-knowledge proof implementations, Ethereum is not limited to the realization of a certain type of zero-knowledge proof, but can support the realization of all mainstream zero-knowledge proof compatibly, maintaining its own openness and expansibility.
The ideal is beautiful, but the truth is always thin, even cruel. When Ethereum was founded, it did not consider the introduction of zero-knowledge proof. Therefore, if Ethereum directly zero-knowledge proof, the biggest problem will be that most of the components of Ethereum protocol will lead to a large number of zero-knowledge proof computation, which does not play the advantage of zero-knowledge proof in essence. Of course, the Ethereum protocol itself can be iteratively updated over time and technology. As with the time-changing consensus mechanism change of PoW to PoS, zero-knowledge proof of Ethereum protocol is possible through Ethereum upgrade in the future.
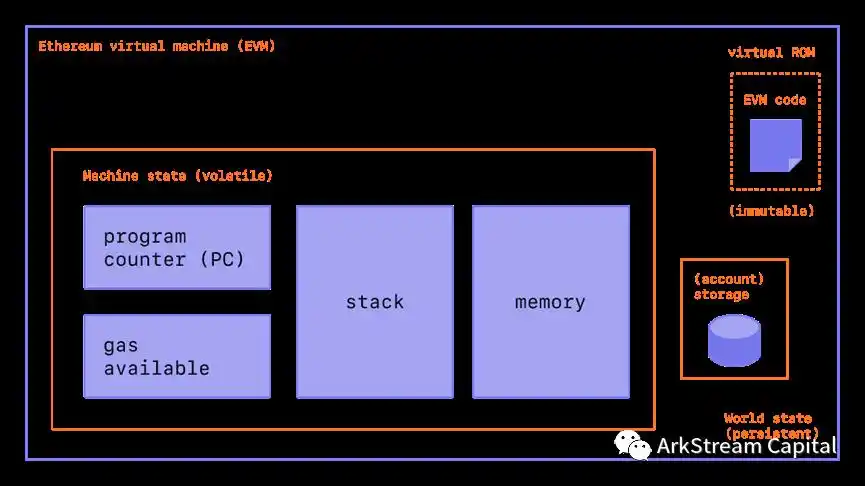
Figure 5: ETHEREUM VIRTUAL MACHINE (EVM)
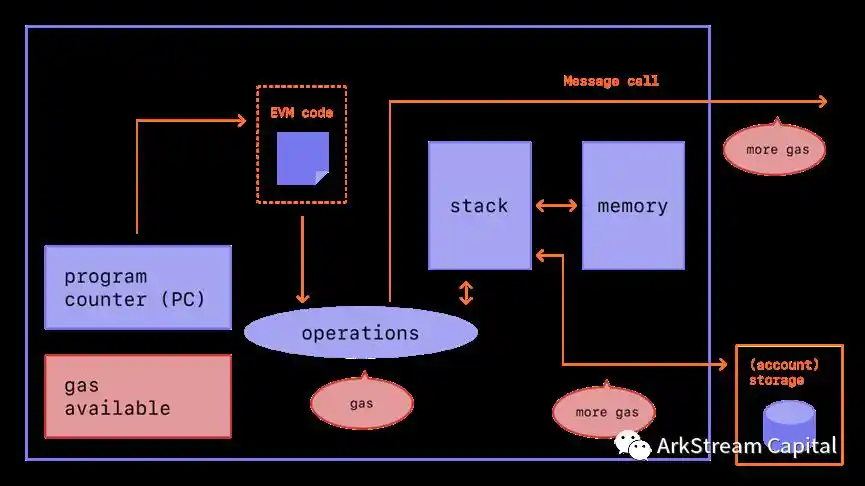
Figure 6: ETHEREUM VIRTUAL MACHINE (EVM)
August 4, 2022, Ethereum founder Vitalik published an article: "The different types of ZK-EVMs". This paper is similar to the previous Ethereum EVM classification proposed by Justin Drake, a fellow of the Scroll group and Ethereum. The following figures provide a clearer understanding of the design and advantages and disadvantages of these zkEVMs/zkVMs.
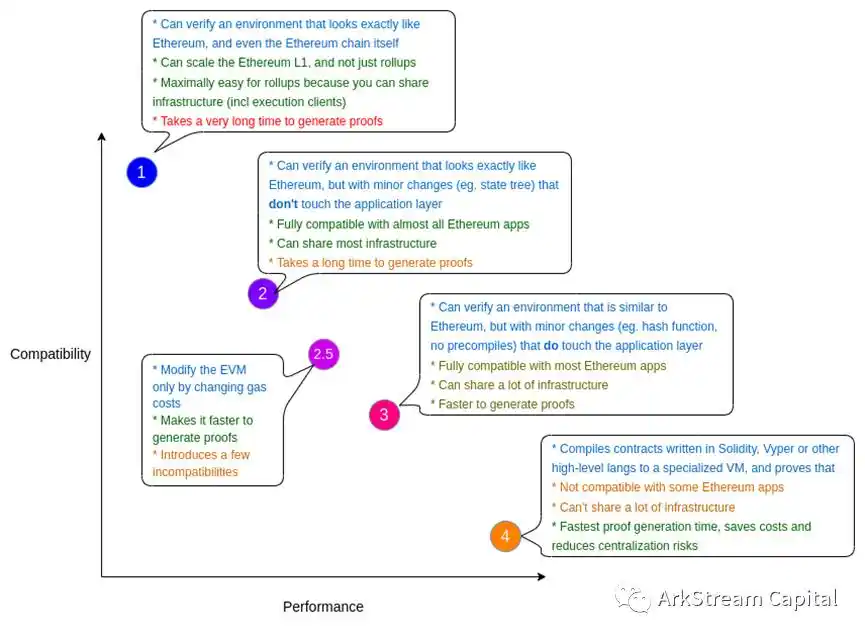
Figure 7: The different types of ZK-EVMs
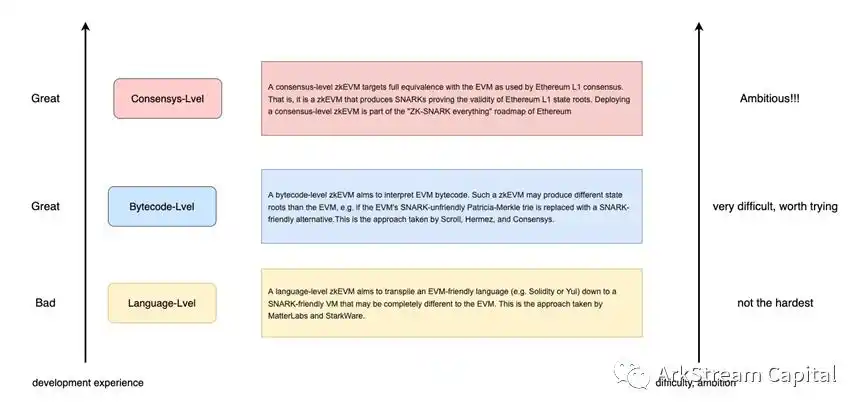
Figure 8
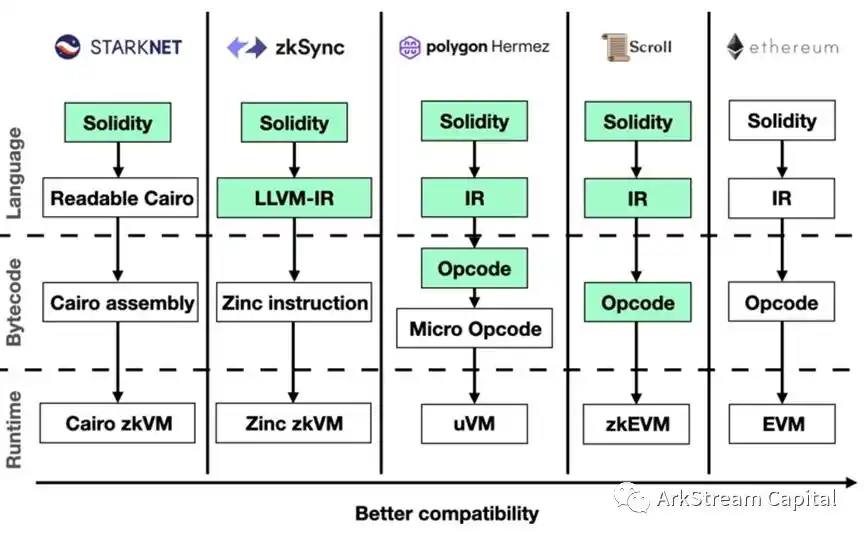
Figure 9
Now let's briefly summarize the progress of the entire zkVMs/zkEVMs technology team or project.
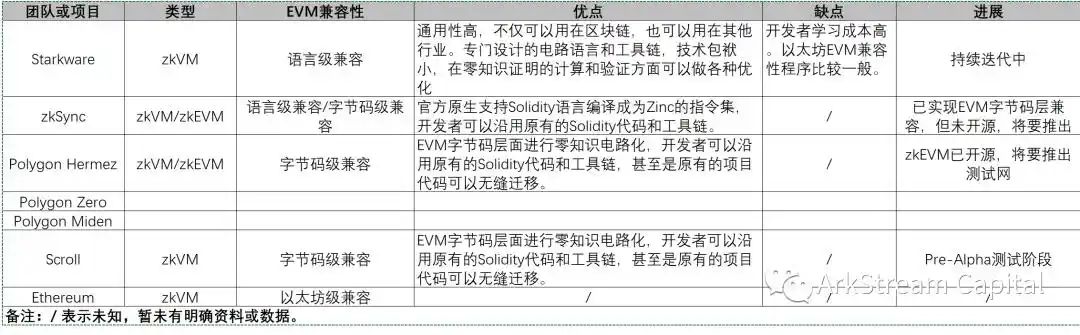
Figure 10
The research and implementation of zkVM and zkEVM face different implementation problems and do not depend on the sequence, so they can be carried out simultaneously. For specific design challenges and solutions, refer to the materials and documentation of each project. Different projects will definitely have their own considerations for choosing zkVM/zkEVM. At present, it seems that most will prefer zkEVM path, after all, the just need scenario of Ethereum expansion has always existed. In addition, Ethereum itself is the ultimate ZK goal, all compatible. With this in mind, zkEVM based research and development projects may evolve into various Ethereum light node clients in the future. As for the zkVM, let's just say that the blockchain is definitely its companion, but its dreams go beyond the blockchain.
Reference materials:
[1] https://github.com/sec-bit/learning-zkp/blob/master/zkp-resource-list.md Zero Knowledge proof learning resources summary
[2] https://mp.weixin.qq.com/s/808jMXvIUqB973aVHrAzGQForesight Ventures: unscramble the zk, zkVM, zkEVM and its future
The design of the study: [3] https://www.odaily.news/post/5178462Scroll zkEVM challenges and solutions
[4] https://www.odaily.news/post/5177903LD Capital: overview of ZK all-star project
[5] https://mirror.xyz/cvalleylive.eth/Deag4YB_EYHaTDv0lc5iPhLpWxzMLG1tyC2GSTwJE4k swastika hardcore reading: why ZK is important?
[6] https://ethereum.org/en/developers/docs/evm/Ethereum Virtual Machine
欢迎加入律动 BlockBeats 官方社群:
Telegram 订阅群:https://t.me/theblockbeats
Telegram 交流群:https://t.me/BlockBeats_App
Twitter 官方账号:https://twitter.com/BlockBeatsAsia
 Finance
Finance
 Specials
Specials
 On-chain Eco
On-chain Eco
 Entry
Entry
 Podcasts
Podcasts

 API/RSS
API/RSS
 Social
Social

 Summarized by AI
Summarized by AI







