Secret Network: What is a programmable privacy public chain
Written by: 0x76@BlockBeats
In the blockchain industry, privacy has always been a very confusing concept. Therefore, before actually introducing today's privacy project Secret Network, it is necessary to reorganize the concept of privacy.
This article will be divided into two parts. The first part re-analyzes privacy and related main concepts. In the second part, we will get started directly and see how the Secret Network, the first public chain that is truly available in the industry and supports privacy programming, differs from other public chains in use.
When we are discussing privacy, what are we talking about?
Privacy is a label that has been surrounding the encryption industry since the birth of Bitcoin. Satoshi Nakamoto also included a separate chapter in the Bitcoin white paper to discuss privacy issues. However, is the privacy provided by Bitcoin really the privacy in our daily life?
Naturally anonymous accounts
We know that currently represented by Bitcoin and Ethereum One of the most important features of the mainstream blockchain network is that all its transaction records are completely publicly verifiable. The only reason why users can still maintain a certain degree of privacy in this extremely transparent environment is its unique account registration mechanism.
For any account system, the most important job is to prevent account duplication. Because once there is a duplicate name, the related information and even the ownership of the assets will be disputed, which will lead to serious confusion in the entire system. Just like the primary key in each table of the database, the accounts in a system must be unique in order for the entire system to function properly.
Therefore, in the general account system, there must be a centralized node, which is responsible for the registration of new accounts, so as to ensure the uniqueness of each account in the system sex. However, because Bitcoin needs to be completely decentralized, other solutions must be adopted.
As we already know, the final answer given by Satoshi Nakamoto is that each user independently generates an address through a random algorithm. So how does the random algorithm prevent duplicate addresses? The answer is that it cannot be prevented at all. What we can do is to reduce the probability of duplicate addresses to a low enough probability, and finally replace the final certainty of the centralized registration mechanism with this decentralized probability and certainty.
And because this generation mechanism is completely random, all addresses have inherent anonymity. This kind of anonymity is the privacy we often talked about in the early days.
However, privacy protection through address anonymity has two important drawbacks. One is the irreversibility of anonymity. Once the real identity of an address is exposed, the loss of anonymity is irreversible.
Another feature is that the work of maintaining address anonymity is completely off-chain. That is to say, after the address is generated, the work of maintaining anonymity is the responsibility of the holder outside the chain, and the blockchain system has no knowledge of anything related and can do nothing.
In this case, the early privacy solutions on the chain can only be retrained by constantly deleting numbers and cutting off the connection between the new anonymous address and the old address. To help users restore their anonymity.
The early privacy projects we are familiar with, such as Tornado.cash, and even Dash (Dash), Monero (XMR, Monero), Zcash ( ZEC, Zcash) and other privacy public chains are basically designed around this idea.
The disintegration of the anonymous account system
However, when the blockchain technology gradually changes from the Bitcoin era After the transition to the era of smart contracts represented by Ethereum, various new applications have been born, and the impact on the original anonymous account system is also increasing.
Earlier addresses were only used to hold purchased cryptocurrencies. Today, we need to use these addresses to purchase NFT avatars, associate social accounts, hold domain names, keep game props, and even publish Mirror articles. All of these activities make it more and more expensive to continue to maintain the anonymity of these addresses, and the transfer work of deleting and retraining again is becoming more and more complicated to the point where it is almost impossible.
So we suddenly found that simple anonymous addresses can no longer meet the needs of users in the new era, and we need more advanced privacy solutions.
What is real privacy?
We no longer have academic discussions on the definition of privacy, here we directly follow the conventional understanding of privacy in life. The privacy we refer to in our daily life does not mean that people wear masks to live every day, but that even if we disclose our identities, we can have our own private space and conduct private transactions when needed.
Corresponding to the blockchain, the privacy we need should preferably be in such a form. Even if my address is already a public real-name address, I can hide the amount of assets I hold according to my own needs, and interact with the DeFi protocol without worrying about the information being disclosed. Although the purchased NFT exists in my own address, it is not You can choose whether to display it publicly or not according to your own wishes.
For this demand, the traditional privacy public chains that cannot support smart contracts are obviously helpless. We need a new programmable privacy public chain to accomplish this mission.
Programmable privacy public chain
Currently in the entire market, it can comply with the support of smart contracts , and there are two public chains that can customize the privacy of transactions on the public chain, one is Cipher Paratime for privacy programming launched by Oasis Labs, and the other is Secret Network, a privacy public chain in the Cosmos ecosystem.
Of course, what we are talking about below is the Secret Network, which has already begun to take shape and is practically available. As Oasis Labs' privacy products still lack available applications, we can only introduce them later when we have the opportunity.
(Note: The Oasis network has different Paratimes. Readers who do not understand the concept of Paratime can simply understand the different Rollups of Ethereum. Many users have only been exposed to Among them, the EVM compatible version Emerald Paratime, and the Cipher Paratime that truly supports privacy programming is still immature.)
Secret Network development history: from Ethereum to Cosmos ecology Application Chain
Secret Network project was named Enigma in the early days, and it hoped to rely on the Ethereum ecosystem for development. Later, after encountering a performance bottleneck, the technical route was adjusted, and an independent public chain that supports privacy computing was developed through the Cosmos SDK. This public chain is now the Secret Network.
Of course, as a member of the Cosmos ecosystem, Secret Network can also seamlessly integrate the IBC cross-chain protocol, which can easily interact with other public chains in the Cosmos ecosystem .
Practical operation of Secret Network privacy function
There are many introduction articles about privacy projects before. I like to use some specious grand concepts, not to explain things clearly, but to confuse the water. Therefore, in the second half of this article, we directly introduce to readers what is programmable privacy directly through hands-on practice.
First of all, Secret is similar to any other smart contract platform-type public chain, and has its own native Token: SCRT, which can be used to pay for transactions on the Secret network fees, and participation in PoS staking. Like other smart contract platforms (such as Juno), SCRT's transfer records are completely transparent, open and verifiable, so there is no privacy attribute at all.
However, unlike Juno, there is a special privacy token in Secret Network, which we call sToken. Every ordinary Token can be packaged into sToken to obtain privacy properties.
In the Keplr wallet, we can also find that unlike other public chains, there are only two options, Stake and Governance, under the Governance tab in the Secret Network column, There is also a Secret SCRT button. Click to see the conversion page from Secret to sSecret.
In this interface, we can directly convert the non-private SCRT tokens held in the wallet into sSCRT tokens with privacy properties.

However, if you are using sSCRT for the first time, you will find that after the conversion is completed, the balance of sSCRT will not be directly displayed in the wallet interface, but the Loading... status will be displayed. This is because in the Secret Network, any sToken is invisible to any visitor by default, including the address holder. If you want to see the balance of sToken, you need to use the wallet to sign the transaction to generate a Viewing Key.
If we refresh this page, the system will automatically pop up the following Add Token transaction signing interface. Add Token here refers to adding sSCRT token, and the contract address displayed on the top of the interface is the contract address of sSCRT.

Click Submit to enter the transaction signing interface. Note that SCRT is required to pay the gas fee for signing any transaction, and sSCRT cannot be used as gas. Therefore, when you are exchanging sSCRT, remember to keep some SCRT balance.

After signing, the system will Generate a Viewing Key for your wallet. After obtaining the wallet corresponding to the Viewing Key, you will have the authority to perform various operations such as inquiries and transfers on the corresponding sToken. Moreover, the addition of the Viewing Key is one-time, as long as the wallet is not replaced later, there is no need to recalculate the Viewing Key.
Just as SCRT has the only corresponding privacy token sSCRT in the Secret Network, any other Token can generate a separate privacy token after entering the Secret Network Certificate sToken, and each sToken corresponds to a unique contract address.
Similarly, when the account receives a new sToken for the first time, it also needs to sign the transaction to generate a new Viewing Key, otherwise the balance of the sToken cannot normal display.
So how does sToken protect the privacy of users when using it? Below we verify some common transactions through the Mintscan browser.
(1) Receive and pay sToken
When an address pays sToken, a transaction record will be left in the browser. Let's take the payment of sSCRT as an example. The address of the payer is publicly visible in the browser. At the same time, we can also know that this transaction involves interaction with the sSCRT contract, but the payee and the transaction amount are not visible.

Let's take a look at the status of the payee. When we confirm that the funds have been received in the wallet, we open Mintscan and find that there is no new transaction in the transaction history. Therefore, no one can find out when and how many sTokens an address has received through public information.
(2) Transaction and Exchange
We use SecretSwap, the native trading platform in Secret Network, to exchange 0.1sSCRT for sATOM.

The following is the record of this transaction in the browser. It can be seen that we can still see the address of the payer and infer that he interacted with the sSCRT contract, but what he did, what tokens were exchanged, and the amount cannot be verified from public records.

However, since we are holding sATOM for the first time this time, we cannot directly see the amount of sATOM we just purchased in the wallet interface. We need to sign another transaction to create the Viewing Key of sATOM before continuing Manipulate the assets we buy.
We go directly to the dedicated sToken conversion website (wrap.scrt.network) officially provided by Secret Network and connect to the Keplr wallet.

You can see that a yellow avatar is displayed on the balance of sATOM on the right No Viewing Key has been created. Clicking the mouse directly here will pop up the transaction signing interface for creating a Viewing Key.

After the signing is successful, we can see the balance of sATOM in the interface and the Keplr wallet plug-in.

At the same time, the signing operation just now will leave a public transaction record. It shows that your address has interacted with the sATOM contract address once, but the specific interaction content cannot be judged.

The above is the public information generated on Secret Network when sToken is used for payment and transaction. It can be seen that by using sToken, users can selectively hide the key information of their transactions to protect the privacy and security of the user's key information.
Bridging Non-Privacy Assets
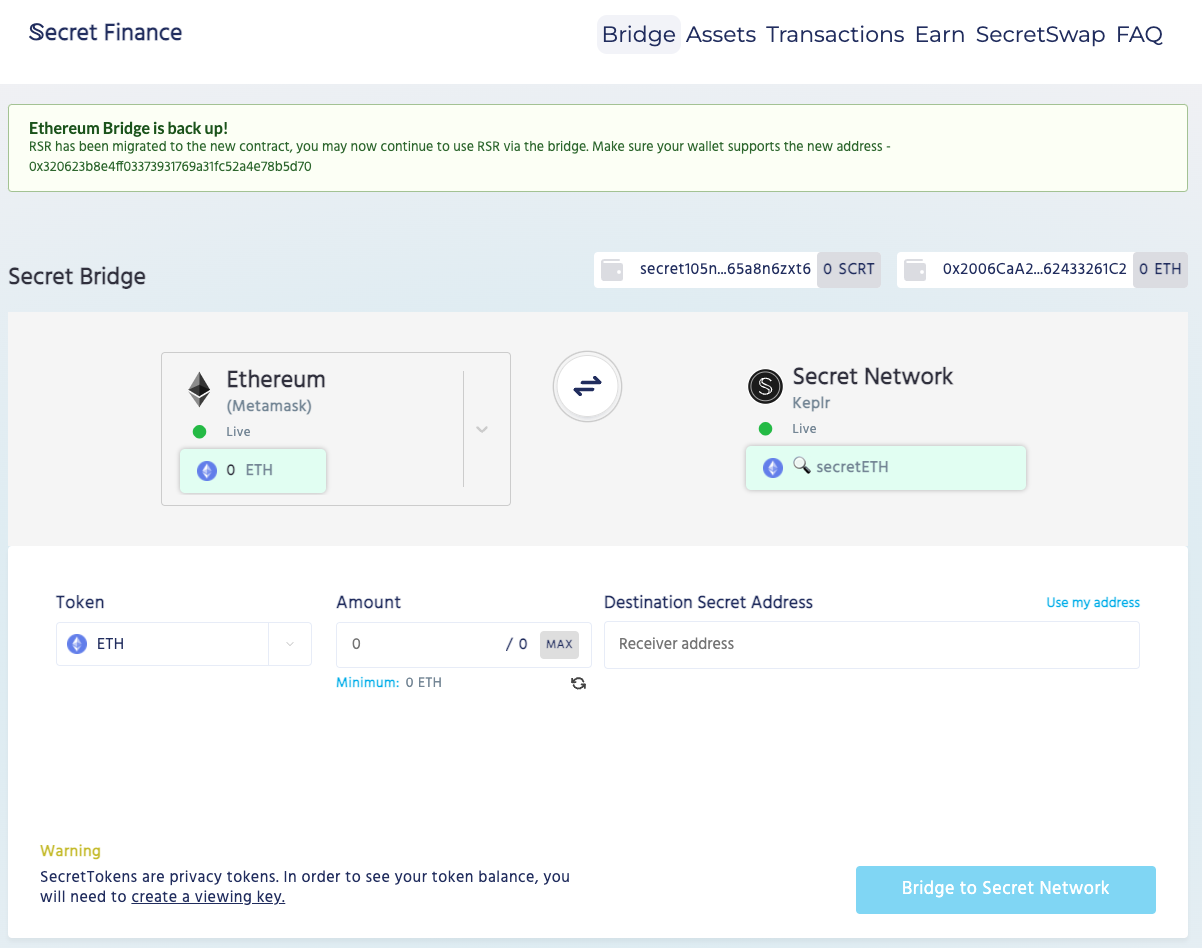
As we just saw Yes, Secret Network can convert any asset into a privacy token, thereby hiding relevant transaction information. So if users want to make their own Ethereum and other public chain assets also have this privacy protection function, they need to cross-chain assets through a cross-chain bridge.
The official cross-chain bridge of Secret Network contains two important components, one is to support IBC The cross-chain packaging bridge, and the other is an official bridge that supports Ethereum, BSC and Monero cross-chain.
(1) IBC cross-chain packaging bridge (https://wrap.scrt.network/)
This bridge is the application we just used when querying the sATOM address. It can not only help users quickly package ordinary tokens into privacy tokens Tokens (the red box in the middle), or through the IBC protocol, rapid asset cross-chain transfers between different Cosmos public chains (red box on the left).

We click on the two-way on the left side of the interface The arrow button directly calls up the IBC cross-chain interface, where you can operate assets into Secret and out of Secret.

After depositing assets, you can directly click the WRAP button on the right to convert it into privacy version of sToken.

(2) Official bridge (https://bridge.scrt.network/)
Secret Network’s official cross-chain bridge has been It supports asset cross-chains of Ethereum, BSC and Monero, and its cross-chain method is similar to that of ordinary cross-chain bridges, so we will not demonstrate it here.
< /p>
Token Standard
< /p>
Secret Network has established a unique privacy pass standard SNIP-20, which is based on the CW-20 standard of Cosmos ecology, which mainly strengthens the privacy function of the original standard. In addition, there is the SNIP-721 standard for supporting privacy functions, which is used to support private NFT issuance.
What is the use of programmable privacy?
After reading the simple experience just now, many readers may have discovered a very important problem. That is: it is very troublesome to operate these privacy applications.
Not only do we need to transfer frequently between the original Token and sToken, but we also need to continuously sign transactions to add Viewing Key. But what is the purpose of making such trouble? In addition to being able to hide how much money is in my wallet (it doesn't seem necessary, after all, I don't have much money in my wallet), what else can Secret Network's privacy computing bring us?
1. Anti-MEV
< br>
If you have ever conducted transactions in Ethereum, then you must have heard of sandwich attacks. That is, when you sign a transaction, since the transaction is publicly visible in the mempool before it is packaged, miners and arbitrageurs can buy before your transaction and sell after your transaction is completed , causing your transaction costs to rise.
In the Secret Network, since the transaction instructions can be hidden, whether it is a miner or an arbitrage robot , MEV can no longer be extracted. The end result is that users can buy the assets they need at a truly fair price.
2. Private NFT
The private NFT on Secret Network can also provide similar functions to sToken. For example, if you bought an extremely precious NFT similar to CryptoPunk, you are worried that it will be discovered by others and carry out targeted phishing attacks on you. In order to protect the security of your assets, you can choose to hide them so that others cannot see the NFT assets you hold in your public address.

(click the key button on the right side of the NFT you purchased to adjust whether to display the This NFT)
At the same time, the NFT on the Secret Network can also choose to transfer the metadata on the chain Perform encryption processing. The minter of the NFT can stipulate that only the holder of the NFT can see the real metadata address, showing a clear picture, while other addresses can only see the blurred picture.
For example, in Secret Network's largest NFT trading platform stashh, we can click on the age on the left After verifying the button, browse private versions of NFT products.

This kind of NFT users can only browse a blurred image before purchasing, and only after you actually purchase, To see the complete NFT metadata.

However, since these products are not cheap, I will not buy them here to show you. Finally, I would like to remind users who want to try to beware of fraud, because the metadata of these NFTs is completely hidden, so you have no way of knowing what is inside before buying.
What are the main issues with Secret Network?
After the above simple experience, we have gained a more intuitive experience of Secret Network . First of all, Secret Network has the basic functions of any smart contract platform, and also supports common application deployment. The current Secret Network ecology includes not only decentralized trading platforms, various DeFi applications, but also NFT casting and trading markets. If the privacy token sToken is not considered, its experience is basically the same as that of the traditional smart contract public chain.
But its flaws are also obvious, that is, it is used to protect privacy sToken gives users an interactive experience had a relatively large impact. New users not only need to understand various new concepts related to privacy, but also need to switch between privacy tokens and non-privacy tokens frequently. If there is no obvious incentive or usage demand, it may be difficult for ordinary users to stick to it.
In addition, not long ago, the DeFi application Shade Protocol on Secret Network issued an airdrop. As a result, the Secret Network network was directly blocked. Not only was the transaction confirmation speed on the main network slow, but many users who extracted SCRT from Osmosis in order to receive airdrops could not receive cross-chain assets for a day or two.
It is also the first time I personally have such a bad experience using IBC cross-chain (of course this is mainly the responsibility of Secret Network). Although the team immediately carried out an emergency update, such transaction processing capabilities are still far from being used on a large scale.Recommended reading
《How easy is the IBC cross-chain in Cosmos? 》
《Juno Network: A Cosmos platform-level project that cannot be ignored》
《Have money every day? What are the ecological benefits of Cosmos 》
《 < /b>Inventory of the latest testnet and incentivized testnet coming to Cosmos in the first half of 2022 》

Welcome to join the official BlockBeats community:
Telegram Subscription Group: https://t.me/theblockbeats
Telegram Discussion Group: https://t.me/BlockBeats_App
Official Twitter Account: https://twitter.com/BlockBeatsAsia


 Forum
Forum Finance
Finance
 Specials
Specials
 On-chain Eco
On-chain Eco
 Entry
Entry
 Podcasts
Podcasts
 Activities
Activities
 OPRR
OPRR









