The first sound of the bull market, BTC L2 will create the king of Alpha.
Original author: blockpunk ∞
Editor's note: There is no doubt that the start of this bull market was marked by the prosperity of the inscriptions. It is foreseeable that the threshold of the Bitcoin ecosystem will become higher and higher in the future. Therefore, the expansion and reduction of BTC fees are urgent. In this article, the encryption blogger blockpunk ∞ has compiled the current mainstream BTC L2 implementation methods for us, and BlockBeats has organized the full text as follows:
【The first sound of the bull market, BTC L2 will create the king of alpha】
This article takes stock of the mainstream BTC L2 implementation methods in the market, and how to introduce BTC assets and security.
In the previous long push, it was mentioned that the great development of "Inscription" has promoted the prosperity of the BTC ecosystem, but it has also intensified the competition for BTC network resources, high fee costs, and the foreseeable rise of BTC in the future, which is constantly increasing the entry threshold for BTC ecosystem players.
This prompted more people to start discussing BTC's scaling solutions, which also caught the attention of the community and investors.
Of course, people have tacitly avoided directly upgrading the BTC L1 expansion plan. The most radical discussions are nothing more than unlocking some OP scripts and continuing to explore the remaining potential of BTC under Taproot (such as discussions on CTV and CAT).
In the development and theoretical achievements of rollup and modularity in ETH, BTC Layer2 has become the mainstream of expansion discussion and the fastest effective solution. The first batch of projects will also go online in the next two to three months and become the absolute mainstream narrative of speculation.
Due to the highly decentralized governance of BTC, there is no "church" to guide the community, so its L2 design is also diverse. This article will start with the typical BTC L2 and related protocols in the market, to explore the possibility of BTC scalability.
Here, BTC L2 is roughly divided into sidechains, rollups, DA layer, decentralized indexes, etc., and similar projects are grouped together for illustration. As there is no authoritative definition for BTC's scaling solution, my actual classification is not rigorous.
This article focuses on exploring implementation solutions, and many designs are still in the conceptual stage. In the competition for second-layer assets, technology and security are the minimum requirements for a project. Technology is the ticket, and it can range from first-class to economy class or even standing room only. When it comes to asset speculation, achieving a passing grade is sufficient.

However, from the perspective of assets, one is the ability of L2 itself to create assets, whether it is introducing inscriptions or pulling plates by itself, which cannot be evaluated solely from a technical level; the second is whether it can attract BTC deposits from L1, which will be the core competitiveness, and this places great emphasis on the security of bridging, after all, "not my keys not my Bitcoins" is a core doctrine, which is very relevant to the scheme design.
BTC's adoption in the ecosystem, will it surpass ETH in the future? Maybe this can give you some reference.
First, it is necessary to introduce the pre-technology. The Taproot upgrade brings two changes:
· Schnorr signature introduced a multi-signature method for up to 1000 participants in BTC, which is the foundation for many L2 bridges.
· MAST allows a group of UTXOs to be combined through a Merkle tree to achieve more complex logic, providing possibilities for proof systems on L2;
· Tapscript has upgraded the Bitcoin script, allowing for the verification of a series of scripts to determine whether UTXOs can be spent, providing possibilities for L2 withdrawals, confiscations, and other operations.
Sidechain
Everything is for usability, and usability is everything.
The advantage of sidechains is that they are effective and prioritize the rapid development of business logic.
Its security is basically only related to its own network, which is a "hanging ticket" on the security train of BTC. The most important part is the cross-chain bridge of BTC, which is the only connection point.
@BTClayer2 BEVM
In fact, most BTC L2 solutions, such as BEVM, follow the idea of sidechains in ETH's scalability expansion.
BEVM deploys a multi-signature address on BTC's L1 through the ability of Taproot, and runs an EVM sidechain, deploying a smart contract that accepts BTC withdrawal requests in EVM. BEVM's GAS uses BTC after cross-chain.
When recharging, the operator of the bridge synchronizes BTC data and notifies the sidechain. The BEVM node also runs a light client to synchronize BTC block headers and verify recharges. When withdrawing, the custodian of the bridge signs and collects a certain number of signatures (threshold) before the transaction to extract BTC is sent out. This achieves asset interoperability between the sidechain and BTC.
@MapProtocol Map Portocol
@BitmapTech Merlin Chain
@dfinity ckBTC
@nubit_org Nubit
@Veda_bitcoin Veda
@babylon_chain Babylon
The previous article mentioned that Nubit plans to use Babylon's BTC collateral service to enhance security. Babylon uses a purely cryptographic solution for handling BTC storage, access, and confiscation, which is highly secure. However, for chains that use collateral services, this imposes constraints on the economic level, and there is still some distance from the verifiability of methods such as ETH's Rollup.
Although the timestamp service uploads L2 data to BTC, directly checking all BTC blocks requires downloading the full node, which has a high threshold. At the same time, BTC L1 does not have smart contracts and cannot verify the correctness of this data.
Rollup
Through Ordinals, Bitcoin can store various data and become a highly secure database. Uploading proof data of Rollup to the BTC network can indeed ensure that it cannot be tampered with, but this does not guarantee the validity and correctness of transactions within Rollup.
The core issue with BTC Rollup is verification.
Most BTC Rollups may choose the method of sovereign rollup (client-side verification), where validators synchronize all data of the Rollup off-chain and verify it themselves.
However, this still cannot utilize Bitcoin's strongest ability, which is the POW consensus of hundreds of thousands of nodes, to guarantee the security of rollup. The most ideal situation, of course, is to allow the BTC network to actively verify the proof of Rollup, like ETH, and reject invalid block data.
At the same time, it is also important to ensure that the assets in Rollup can be extracted to the BTC network in the most extreme cases of untrustworthiness, even if the nodes/sorters of Rollup are constantly down or refuse to accept transactions, they can still be safely withdrawn through an escape channel.
For BTC that does not have smart contracts and only executes scripts, it may be possible to use the ability of MAST to combine scripts into logical circuits for verification, although it is difficult, it belongs to the most native idea of BTC.
@ZeroSync_ BitVM
BitVM is the most popular extension protocol on BTC and is an optimistic rollup for BTC.
BitVM innovatively proposed a way to conduct fraud challenges on BTC, where the prover and challenger both deposit an equal amount of BTC as input in a transaction, and the output of this transaction will contain a logical circuit.
The script of BTC can be regarded as logic gates that process the simplest logic, which is the most basic component of a computer. If logic gate circuits are combined in a tree-like manner, a circuit that includes specific logic can be formed (you can imagine the computer in The Three-Body Problem by Liu Cixin).

BitVM has written a fraud proof into a circuit composed of a large number of BTC scripts. The circuit structure of this proof is determined by a series of nodes packaged by the sorter in Rollup.
Challengers can continuously upload hash values to this fraud-proof circuit, while verifiers continuously run corresponding scripts and reveal outputs to prove their results are correct.
Under a series of transactions, challengers can continuously challenge the verifier until the verifier proves that each circuit gate is correct. As a result, the BTC network completes the verification of Rollup, and the verifier can claim their funds. Otherwise, the challenger will receive the BTC pledged by the verifier.
In an easy-to-understand way, the relationship between BitVM and BTC is similar to that of OP to the ETH network, with its security being the highest among all scaling solutions. BitVM generates a huge number of transactions, which are costly, and requires a lot of pre-signing before on-chain verification by participating parties, which involves a lot of off-chain computation.
Of course, unlike ETH's optimistic/zk rollup, BitVM does not have an emergency BTC withdrawal channel. At least one honest node in the L2 network is required to complete a normal exit. However, this is currently the highest level of security that BTC L2 can achieve. After uploading the DA, BTC L1 verifies the validity of the Rollup data, and the BTC bridge minimizes trust, but lacks an "emergency escape channel".
Therefore, the implementation of BitVM seems distant, but the recent discussion in the BTC community about lifting the ban on the op_cat script may bring new possibilities for the development of BitVM. The op_cat opcode can concatenate two strings, supporting a maximum length of 520 bytes. This concatenation of data can enable more complex calculations on Bitcoin. For example, BitVM can concatenate hundreds of logic gates in the same script using it, allowing BitVM to process more binary circuits in fewer transactions, achieving almost a hundredfold increase in speed.
BitVM has inspired many L2 projects with its complex combination of Bitcoin scripts, and many have proposed new approaches to "fraud-proof" challenges on BTC based on this.
@Bison_Labs Bison Network
Bison Network is a Bitcoin-based ZK-STARK sovereign Rollup (client verification).
The so-called sovereign Rollup refers to using L1 as the data availability (DA) board for Rollup, without verifying the correctness of Rollup transactions, which are verified by the nodes of the Rollup itself.
Bison submitted Rollup's zk proof to BTC Ordinals in the encryption industry. Users can download the proof from BTC and run their own client to verify Rollup transactions. If it is necessary to verify the entire state of Rollup, it is necessary to synchronize the full node.
Bison's feature lies in its implementation with the BTC L1 bridge. When a user deposits BTC into Bison Rollup, the BTC is divided among multiple multi-signature wallets that contain BTC. These multi-signature wallets all support DLC (Discreet Log Contracts), a technology based on the Taproot upgrade that utilizes simple logical contracts using BTC multi-signature and time-locked scripts.
When users deposit BTC, they need to sign relevant execution transactions with Bison Network for all future situations, such as transferring to others, withdrawing to the BTC mainnet, and long-term unclaimed situations.
After signing, these transactions will not be published to the BTC blockchain. In order for the transactions to be executed, an oracle is needed to drive them. There are three controllers of the multi-signature wallet: the user, Bison Rollup, and the oracle. With any two of the signatures, control of the BTC can be obtained.
DLC is like an if-do statement on Bitcoin. The oracle inputs the condition of the if statement, and the execution part of the do statement is to send transactions under the three signed scenarios mentioned above.
Here, the oracle is linked to the bridge contract of Bison Rollup. If the bridge receives a request from a user to transfer BTC to someone else, the oracle will send a transaction that has been signed before. The control of the multi-signature address is given to the Bison network for further distribution. If a request is received from the user, the control is transferred to the user. If no message is received for a long time, the time lock expires and the control returns to the user.
As a result, Bison has implemented the extraction of BTC from Rollup and established a simple escape route. However, the weak point of this system lies in the oracle. If incorrect information is passed, it may result in the loss of user assets. Therefore, it may be worth considering the introduction of decentralized components, such as Chainlink.
The "trustless bridge" implemented by DLC is the exploration of the potential of BTC scripts. http://DLC.link uses it to enable BTC to be used across chains such as ETH and STX.
Bison Rollup has implemented a simple "escape route" by introducing new third parties, but still has not achieved BTC L1 verification Rollup proof.
@BsquaredNetwork B² Network
B² Network is a zk Rollup on BTC that incorporates "commitment challenge". The network is divided into two layers, the Rollup layer and the DA layer.
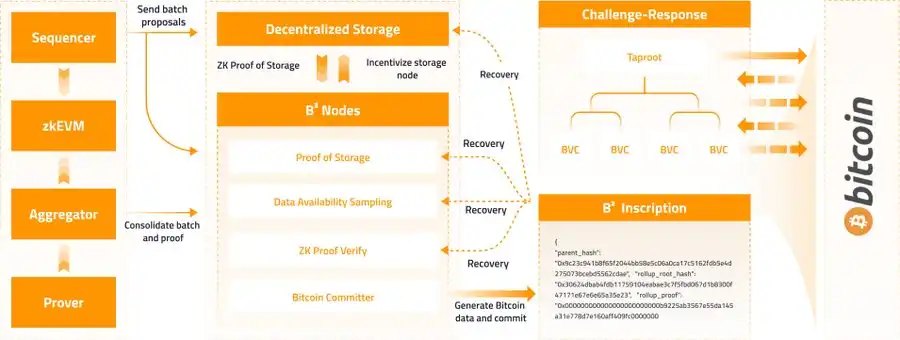
@SatoshiVM SatoshiVM
@chainway_xyz Chainway

@QEDProtocol QED Protocol
Welcome to join the official BlockBeats community:
Telegram Subscription Group: https://t.me/theblockbeats
Telegram Discussion Group: https://t.me/BlockBeats_App
Official Twitter Account: https://twitter.com/BlockBeatsAsia


 Forum
Forum OPRR
OPRR Finance
Finance
 Specials
Specials
 On-chain Eco
On-chain Eco
 Entry
Entry
 Podcasts
Podcasts
 Data
Data





