Technical explanation of how io.net was hacked
Original title: "How Ionet was hacked"
Original author: Holegots, crypto KOL
Editor's note: Yesterday, according to community user feedback, hackers directly modified the names and online status of multiple io.net machines through the API to pollute data. The names and online status of multiple machines were modified. Ahmad Shadid, founder and CEO of io.net, responded later that hackers could only change the user's device private name, and no one ran any new containers on the machine. The official will fix this problem as soon as possible. Crypto KOL Holegots analyzed how io.net was hacked from a technical perspective and said that there is no need to worry about the current situation. BlockBeats reproduced the full text as follows:
Today I saw that a hacker had modified all the devices of ionet, and everyone was panicked. In fact, this is not difficult. The main reason is that io's own security awareness is too poor.
I will roughly talk about how he did it.
IO workflow
First, analyze the workflow of IO worker. In fact, there are mainly three parts, namely data capture and reporting Uptime (but it has been removed in the new version)
Initialization
At the beginning of startup, io.net will go to Secret's API to request a lot of configuration information, which includes the latest image, startup command, and AuthKey for each API call.
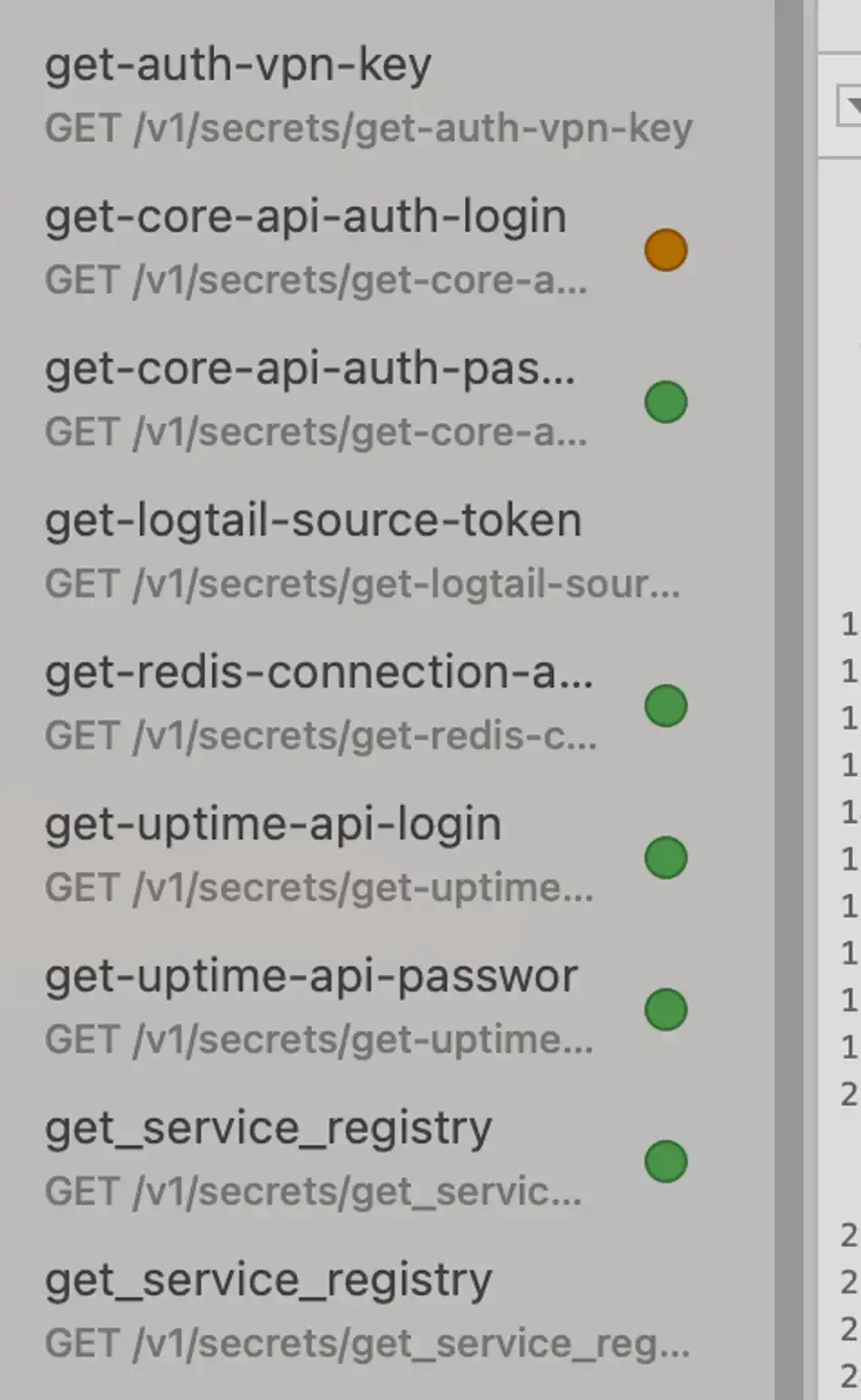
Data capture
Some packages and codes for data capture
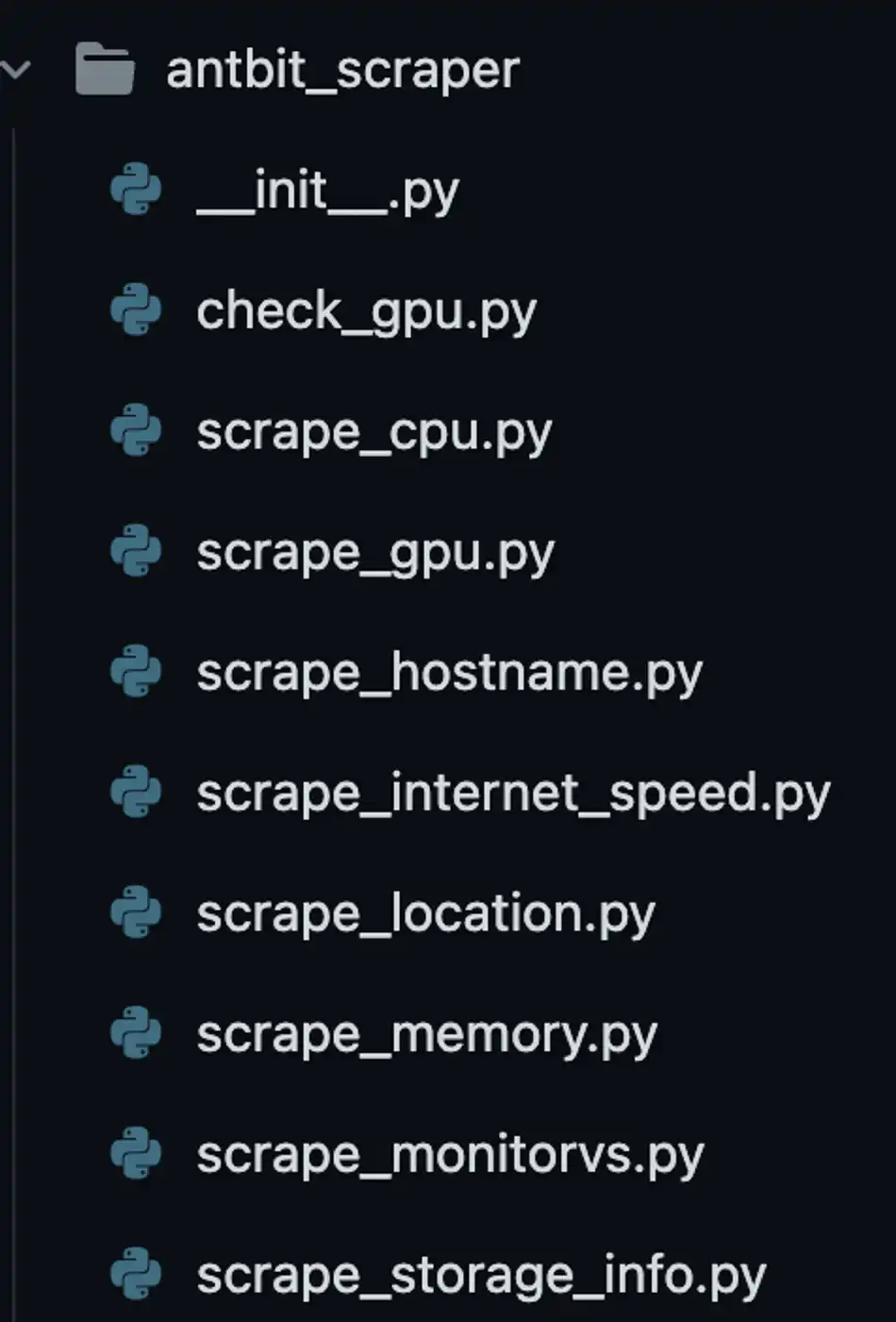
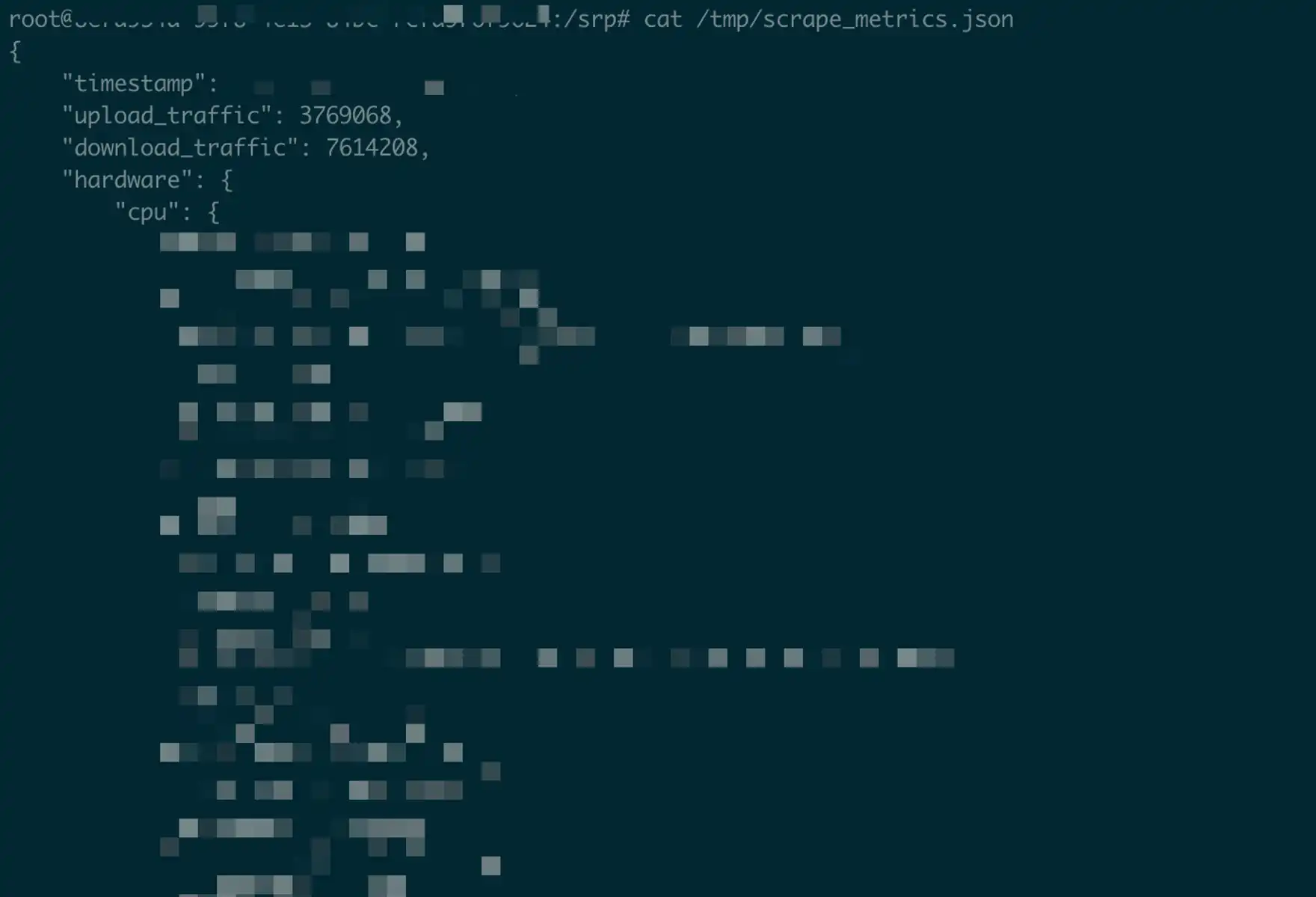
The content is very simple, mainly a series of device information capture, and the capture results can also be seen in the container's /tmp/scrape_metrics.json.
Data reporting
/tmp/scrape_metrics.json
Then there is data reporting, which is also one of the main methods used by hackers. They will write data to two DBs, Redis and Postgresql.
Data insertion in Postgresql
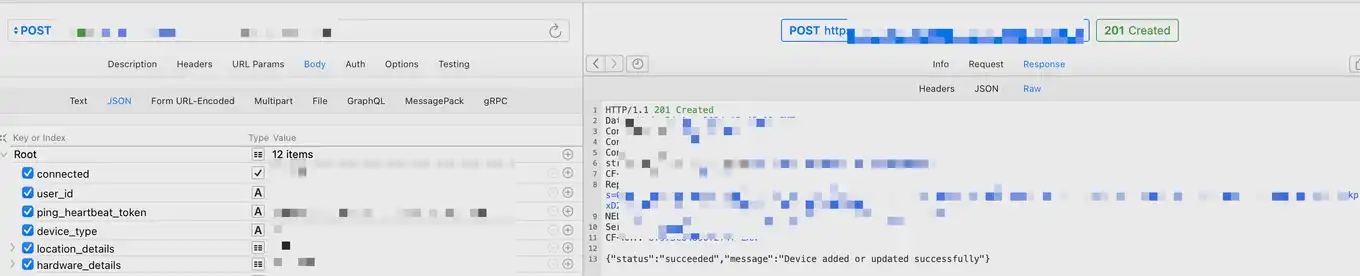
The second is Redis Put and modification, which is mainly for the display and query speed of the front-end page. This is also one of the main modification targets of hackers. This interface is relatively simple and only requires a Device ID
Redis modification and TTL overwriting
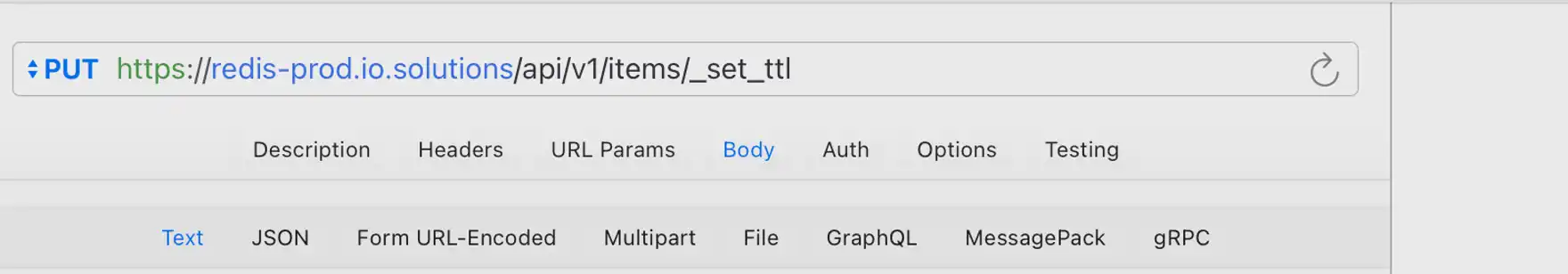
The above is the main process of how IO.net's Worker works.
How hackers contaminate other users
This actually mentions what I just said, io.net’s own security awareness is insufficient. In the above-mentioned reporting interface, there is basically no authentication. You only need to get USER_ID and DEVICE_ID to manually report the device. Of course, this is also the reason why so many devices were added before, because one HTTP Call is enough
Device reporting interface
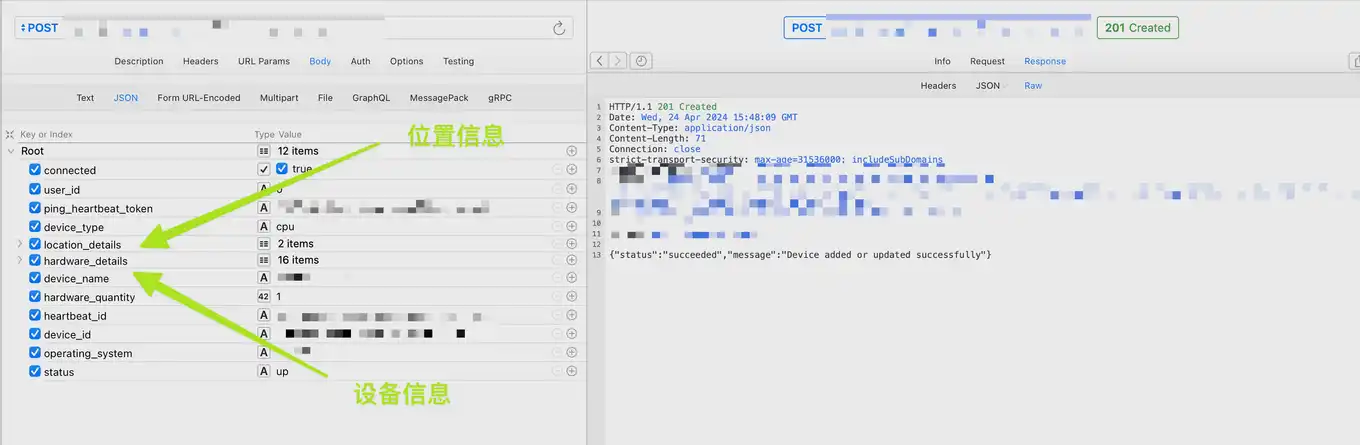
Here you only need to provide USER_ID and DEVICE_ID to insert a new device into the official, and then it’s a question of how to obtain this information
Obtaining Device ID
In the official Explore, you can see the information of all Devices. By traversing the interface, we can also get all DEVICE_ID
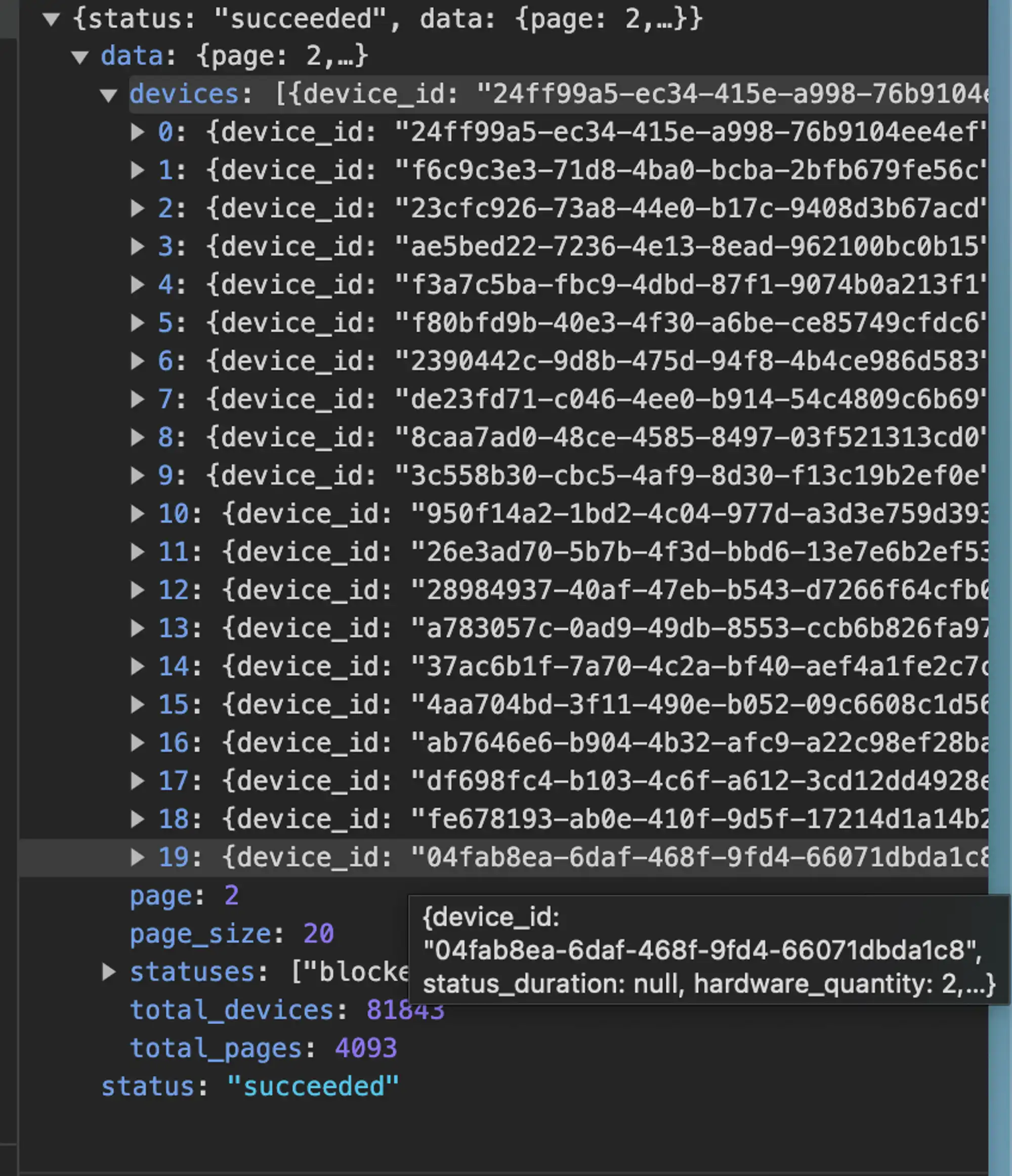
Get USER ID
Note: This method has been reported to the official security team and has been fixed a few days ago.
The principle is very simple. During the initialization of the earliest Worker, the device will obtain its own status. For example, if it is terminated or other status, it will stop running. This interface has always been able to obtain User ID.
Early interface
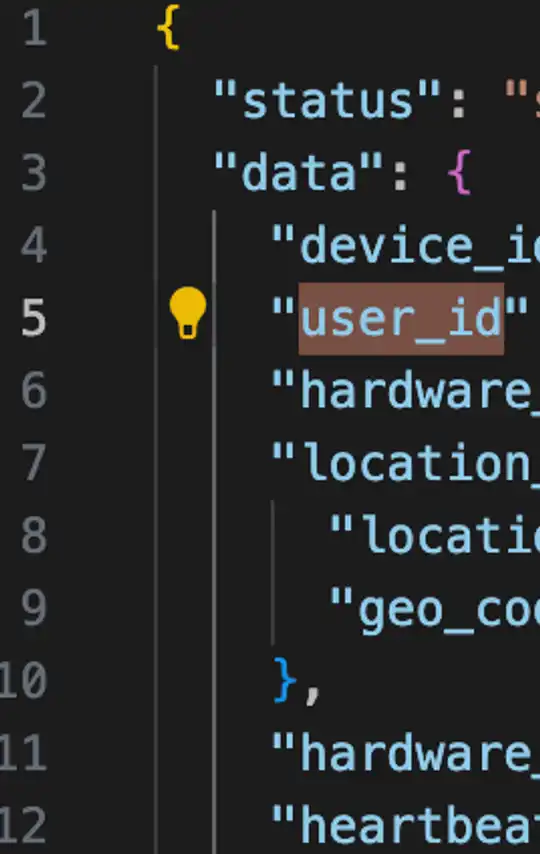
So, a few days ago, you only need to use DEVICE_ID to get everyone's USER_ID,
You only need to get these two IDs to report the corresponding device at will.
Accessing other people's networks
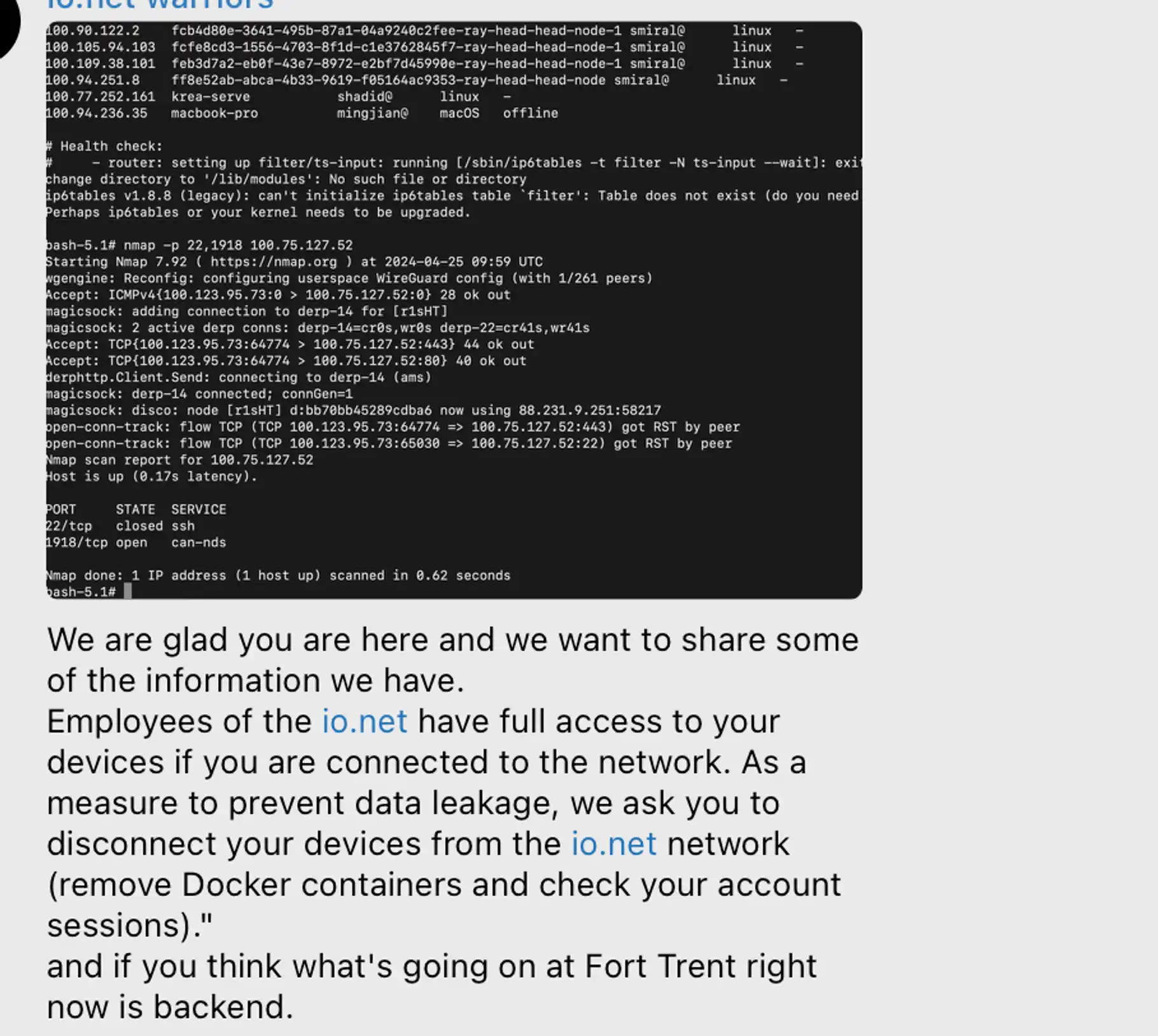
Here is actually a nmap scan after joining tailscale, which can only be regarded as the self-entertainment of the script kid.
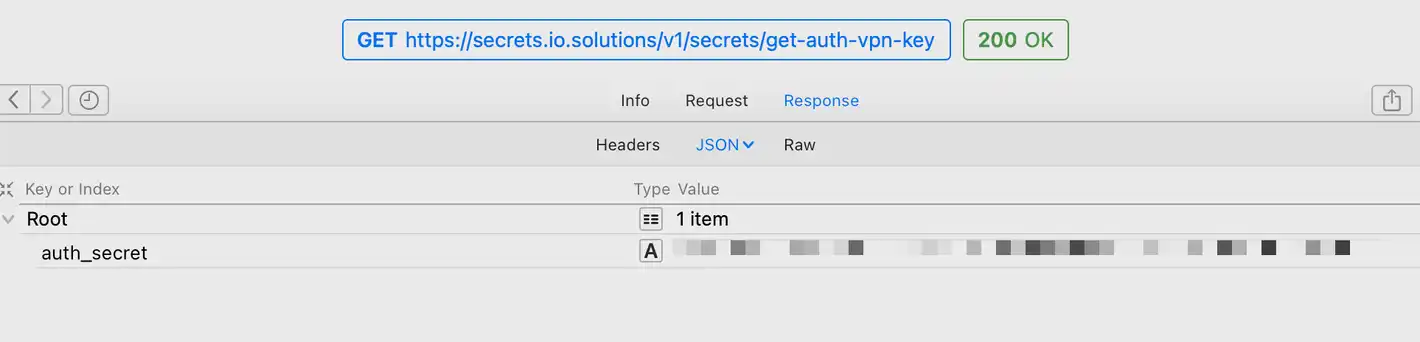
Since io.net uses Tailscale for communication between networks, and the AuthKey will be sent to the device during the initialization process, you only need to get the Authkey to join the network, so everyone can do the same thing.
Don't worry, your device will not join tailscale when it is not in use.
Summary
Should we panic?
As for the whole process, it is not difficult. As long as you are willing and have some network security knowledge, everyone can do it easily.
Since io.net does not do Auth for the PUT/POST interface, the whole performance is like the DB has been hacked, but in fact, only the reported data, wallet and AuthN are affected. It seems that there is no need to worry at all.
Why today?
I personally guess that it may be because the verification of the POW part was added to the image of [io.net](<http://io.net>) yesterday, so it will be more difficult for some script kiddies, so they chose to start the attack today.
Original link
Welcome to join the official BlockBeats community:
Telegram Subscription Group: https://t.me/theblockbeats
Telegram Discussion Group: https://t.me/BlockBeats_App
Official Twitter Account: https://twitter.com/BlockBeatsAsia


 Forum
Forum Finance
Finance
 Specials
Specials
 On-chain Eco
On-chain Eco
 Entry
Entry
 Podcasts
Podcasts
 Activities
Activities
 OPRR
OPRR







