Introduction
System transparency is the key to the normal operation of the blockchain. The so-called transparency means that every node in the network can store a copy and has the right to verify whether there are any violations. In many distributed ledgers, anyone can load a block explorer and browse the blocks, transactions and addresses in the network.
From a privacy perspective, this approach is not ideal. In systems like Bitcoin, each transaction can be linked to previous transactions. Tokens are technically not fungible, meaning each token is tied to a specific transaction. No one can stop you from sending Bitcoins, but if those coins ever pass through a blacklisted address, the other party has the right to reject the transaction.
In the worst-case scenario, a lack of homogeneity can have profound consequences for the foundation of the system. Clean coins gain a premium, while early coins lose value due to historical issues.
Bitcoin’s privacy is often exaggerated. In fact, both tokens and users in the system are traceable. People are accustomed to operating anonymously (showing a public address instead of a name), but there are certain drawbacks to this approach. With ever-increasing precision, cutting-edge analytics aggregate entities across the network for deanonymization.
Confidential transactions are an upgrade to promote truly private transactions.
What is a confidential transaction?
The concept of Confidential Transaction (CT) came out in 2013 and was first proposed by Adam Back, CEO of Blockstream, and was later adopted by Bitcoin Coin developer Gregory Maxwell expanded the extension. In the first part, Maxwell outlined the mentioned problems of "homogenization" and "weak anonymity" and proposed corresponding solutions. He pointed out that the transaction amount can be hidden in the wider network, and only the transaction participants can know the specific value.

In Under normal circumstances (transactions can be viewed publicly), nodes can easily verify that the amount of tokens received exceeds the amount sent. For example, Alice wants to send 0.3 BTC to Bob, she uses the unspent output (let's call it "1 BTC") and splits it into two parts: 0.3 BTC to Bob and 0.69 BTC to send back to the personal wallet (the remaining funds are mined as Mining fees are paid).
For other nodes, this is a simple algebra problem: 1 > 0.3+0.69, the signatures are all correct, and Alice The input is not spent elsewhere, so the transaction must be valid. After the amount was hidden, things became complicated. How do we determine whether an unknown amount is greater than or equal to the sum of two other unknown amounts?
Overview of cryptographic principles involved
In order to hide the data, some encryption technology must be applied. However, the traditional method is similar to storing documents in a safe: once locked, they cannot be taken out until unlocked. Confidential Transactions operate similarly to a digital safe, where the contents are hidden and ownership of assets can be verified by outsiders.
The answer lies in "homomorphic encryption", a mechanism called Pedersen's promise. This type of encryption allows outsiders to perform operations on the encrypted data for various purposes without being able to view the specific content.
A regular hash can be used to submit the data you wish to display. Let’s say you want to announce a contest on social media to win 0.01 BTC for guessing your favorite exchange. Participants may be skeptical about the contest because you can definitely look at their answers after the contest and pick an exchange that no one mentioned.
To do this, you can provide your fans with a hash value: a seemingly random combination of numbers and characters (corresponding to a specific input), via The specific function is passed the answer (i.e. the specified exchange) and finally the output is obtained. Let’s take the SHA256 algorithm as an example:
f1624fcc63b615ac0e95daf9ab78434ec2e8ffe402144dc631b055f711225191According to the above hash value, you do not know the specific input, nor can you get the previous input through the function inversion. But if you know that the input is "Binance" you can easily determine that its hash matches the one listed above. This way, fans will feel more comfortable knowing that you won't change your answer at the end of the game, which would result in a completely different output.
Actually, this method is not absolutely safe. While fans can't reverse engineer the algorithm, they can create a list of exchanges and match the hashes one by one until they get the correct answer. To avoid such operations, we can add random data, called a "masking factor", to the data that needs to be hashed.
If we enter "Binance is my favorite exchange, more than any other exchange2#43Wr ", it will be difficult for competitors to guess the result (after all, they cannot make countless attempts for a mere 0.01 BTC).
With the help of Pedersen promise, we can add input after the promise. Maxwell explained this as:
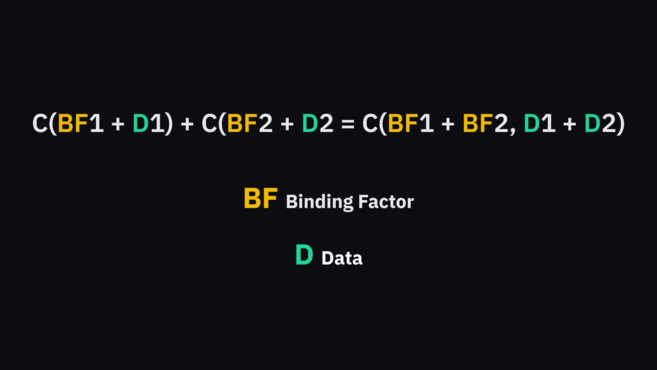
C(BF1 + D1) + C(BF2 + D2) = C(BF1 + BF2, D1 + D2)
whereBFrefers to Occlusion Factor , while Drefers toData
The next few steps involve elliptic curve cryptography and range proof, but the basic idea is still to perform Pedersen commitment processing on the address. When sending funds, the system will generate two additional "commitments" (the change address and the destination address for returning the funds).
No one knows the amount sent, but one can check the change and target commitment (left side of Maxwell's equation) against the original address (equation ) are equal. If the calculation is correct, it is sufficient to prove that the input and output are equal, indicating that the user's transaction is valid.
What can be achieved with confidential transactions
If confidential transactions are applied in Bitcoin, then A more private system can be created. Inputs and outputs in the system will be hidden, and entities in the ledger will be obfuscated, but nodes can still verify their authenticity. With significantly improved privacy, chain analysis cannot reveal the history of a given unit, making Bitcoin effectively fungible.
As for whether "confidential transactions" can be integrated into the agreement, it seems unlikely at present. With the addition of this feature, the size of transactions will be larger than regular transactions, which will naturally create more market demand given the limited block space. In addition, a majority of participants in the network must agree to change the code, which has been a problem in the past.
Summary
Some cryptocurrencies have iterated to some extent with confidential transactions in Bitcoin sidechains. For example, Monero perfectly integrates confidential transactions with the "ring signature" structure to achieve anonymity and homogeneity. The privacy of Liquid sidechains and MimbleWimble has also been significantly improved.
Confidential transactions do have many advantages, but they also face the problem of increased processing volume. Cryptocurrencies have long faced challenges in terms of scalability and throughput of the base layer, and large transaction volumes will also prohibit many people. Nonetheless, privacy advocates argue that it is necessary to hide transaction amounts and participants in order for cryptocurrencies to become truly homogeneous currencies.


 Forum
Forum Finance
Finance
 Specials
Specials
 On-chain Eco
On-chain Eco
 Entry
Entry
 Podcasts
Podcasts
 Activities
Activities
 OPRR
OPRR
